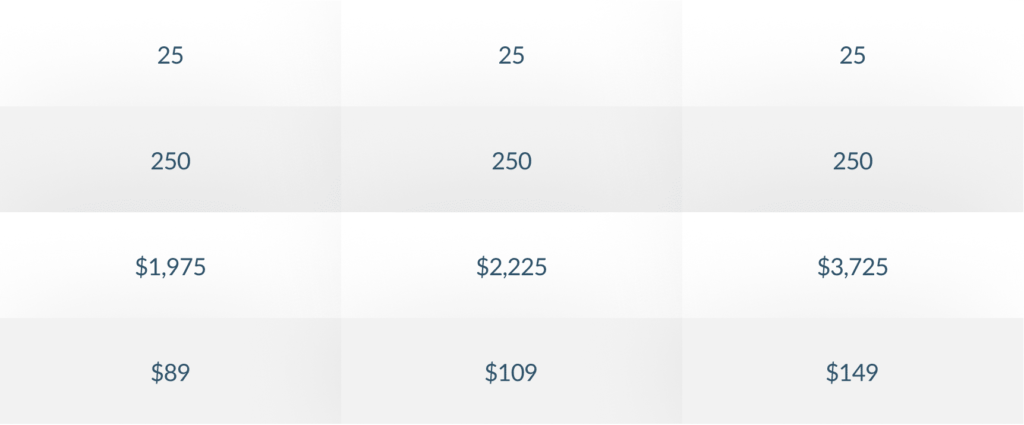Claratti’s enterprise-grade protection, 24/7 monitoring and real-time threat response shields your business from cyber threats, so you can focus on what matters most.
Discover How Claratti Protects Businesses Like Yours in Real Time
Watch to discover how our fearless cyber security team provides round-the-clock protection, real-time threat response, and seamless recovery — so you can focus on growing your business.
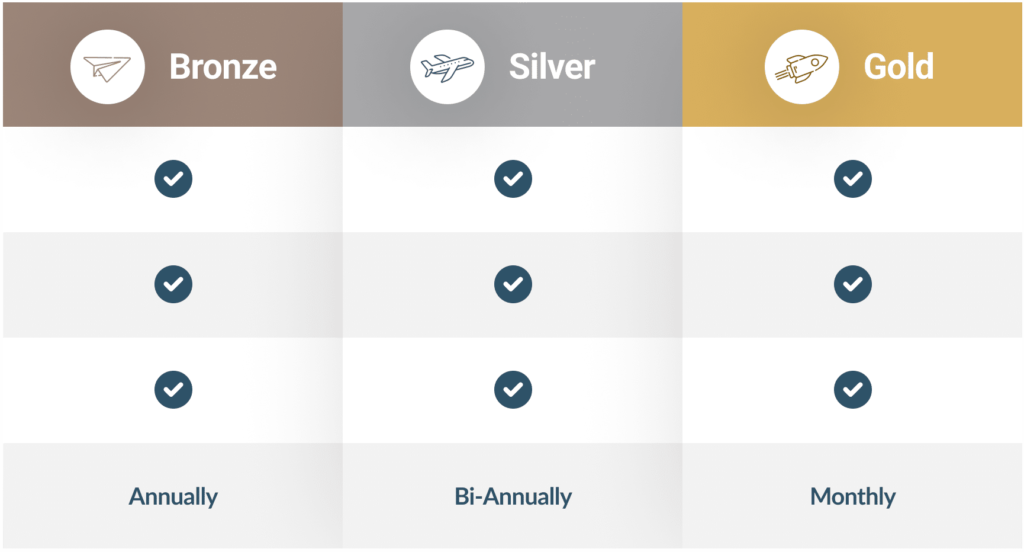
The right package depends on the size of your organisation, the complexity of your IT environment, and your cybersecurity needs.
- The Bronze package is ideal for small to medium-sized businesses that need foundational protection, including firewalls, IT support, and annual security testing.
- The Silver package is better suited for organisations that require more advanced protection, including 24/7 monitoring and data loss prevention.
- The Gold package is designed for larger businesses or those with more critical security requirements, such as those managing mobile workforces or handling
- highly sensitive data. It includes mobile device management and more frequent security testing.
We recommend an assessment of your business’s current cybersecurity posture to help you choose the best package for your needs.
Yes, we do offer cybersecurity awareness training for businesses. One of the most effective defences against cyber threats is ensuring your team knows how to identify potential risks, such as phishing emails, weak passwords, or suspicious activity. Our training is designed to empower your employees with the knowledge they need to keep your organisation secure and to comply with industry best practices.
Cyber insurance is an important consideration if your organisation stores sensitive data, processes financial transactions, or relies heavily on IT systems. It provides financial coverage for losses related to cyberattacks, data breaches, and other security incidents. To determine if you need cyber insurance, you should:
- Assess the level of risk associated with your business operations. Are you handling customer data or personal information that could be targeted?
- Consider the financial impact of a potential breach. Could your business recover from a major cyber incident without significant financial strain?
- Review any regulatory requirements for your industry. Some sectors, such as finance or healthcare, may have legal obligations for insurance or data protection. We can help you evaluate your cybersecurity posture and recommend whether cyber insurance is a smart choice for your business.
- Please call us and book a time to talk to us about our Virtual Chief Information Security Officer (VCISO) services.
Managed Firewall Protection is a core cybersecurity measure that shields your business from unauthorised access by blocking harmful or suspicious traffic at the network’s entry point. It acts as your first line of defence against cyber threats, ensuring that only safe data passes through to your systems. This service is managed by a team of cybersecurity experts, so you don’t have to worry about updates or configurations.
Support & Maintenance in the context of cybersecurity ensures that your systems are continuously protected and operating securely. It includes expert assistance with security-related issues, updates to security software, and regular maintenance to prevent vulnerabilities. If there’s a problem or potential cyber risk, our team is ready to assist and resolve it quickly.
Remote Monitoring & Maintenance (RMM) is a proactive cybersecurity service that continuously monitors your IT environment for potential threats and security issues. It allows our security team to detect and address issues before they cause damage, including vulnerabilities, malware, or system failures. It’s like having an all-seeing eye on your business systems to ensure they remain secure 24/7.
The Security Operations Centre (SOC) is a team of cybersecurity specialists who monitor your systems around the clock to detect and respond to cyber threats in real time. With a SOC, you get full-time protection, even during off-hours, ensuring any suspicious activity—such as hacking attempts or malware—is dealt with immediately to minimise damage.
Cyber Penetration Testing (CPT) is an in-depth cybersecurity assessment where ethical hackers simulate real-world cyberattacks on your systems. This testing identifies weaknesses in your defences that could be exploited by cybercriminals. Regular penetration testing ensures that your security is always up to date and prepared for the latest threats, whether testing happens annually, bi-annually, or monthly depending on your package.
Data Loss Prevention (DLP) is a cybersecurity feature that stops sensitive information from being leaked, stolen, or shared inappropriately. DLP monitors and controls data as it moves through your business, ensuring that confidential information—such as customer data, financial records, or intellectual property—stays protected. For example, if someone tries to send sensitive files outside the company, DLP will block that action to prevent data breaches.
Mobile Device Management (MDM) enhances your cybersecurity by protecting company data on mobile devices like smartphones and tablets. It allows you to secure these devices remotely, control the apps and data they access, and wipe data from lost or stolen devices to prevent unauthorised access. MDM is especially crucial if employees use mobile devices to access sensitive company information from outside the office.
The more frequently Cyber Penetration Testing (CPT) is performed, the better your protection against new and evolving cyber threats. Annual testing provides a good baseline for most businesses, but bi-annual or monthly testing ensures continuous updates to your security defences. With cyberattacks becoming more sophisticated, frequent testing helps catch vulnerabilities before they are exploited.
Data Loss Prevention (DLP) protects against data breaches, accidental leaks, and insider threats. It ensures that sensitive data like personal information, business secrets, and financial details are not shared or accessed by unauthorised individuals. DLP blocks attempts to move, copy, or share sensitive information outside of approved channels, reducing the risk of cybercriminals getting hold of your data.
If your employees use mobile devices to access company systems or data, Mobile Device Management (MDM) is essential for keeping that data secure. It ensures that mobile devices comply with your company’s security policies and protects them from malware, unauthorised access, and data theft. MDM also allows you to remotely lock or wipe lost or stolen devices to prevent sensitive data from being compromised.
Backup & Recovery focuses on creating secure copies of your data so that it can be restored in case of accidental loss, system failure, or cyberattacks like ransomware. It’s a crucial part of any cybersecurity strategy because it ensures business continuity.
Data Loss Prevention (DLP), on the other hand, actively monitors and prevents sensitive data from leaving your network in unauthorised ways. While backups help recover lost data, DLP ensures that data doesn’t get leaked or stolen in the first place.
Restoration & Clean Room our restoration of data is second to none, as we provide advanced level “clean room-style” recovery options, where we check file & directory level analysis, file comparisons and 100’s of other test which allows you to rest easy knowing what has been restored is safe and ready for operation.
With 24/7 monitoring from a Security Operations Centre (SOC), your business is protected at all times, not just during work hours. Cyberattacks can happen anytime, and having a SOC means any suspicious activity is detected and handled immediately—before it becomes a serious breach. This constant vigilance reduces the risk of damage or data theft from attacks like ransomware or phishing.